As usual, the world watched the United States elections on November 8. Donald Trump won the election and started as the 45th US president, contrary to expectations and surveys.
The results of the elections surprised the international community. Meanwhile, interestingly, “The United States Intelligence Community officially concluded that the Russian government interfered in the 2016 United States elections”.[1]
To test this hypothesis, it is helpful to examine the pre-election period and evaluate the results. What happened before the United States elections?
June /July 2016,
Russian government hackers penetrated the computer network of the Democratic National Committee (DNC) and gained access to the entire data base of opposition research on Grand Old Party (GOP) presidential candidate Donald Trump, according to committee officials and security experts who responded to the breach.[2]
DNC officials and the security experts stated that the intruders so thoroughly compromised the DNC’s system that they were able to read all email and chat traffic. Following these events, on July 22, 2016, WikiLeaks began to publish e-mails obtained from the server by hackers. (https://wikileaks.org/dnc-emails/)
October 21, 2016,
On Friday (October 21st), Russian and Chinese hackers started an unprecedented cyber attack on the United States, targeting more than 14 million IP addresses. (Who are the Russian and Chinese computer hackers, the methods of attack and their sources will be explained in another article to be covered in the coming periods) More than 78 percent of the country lost the internet access. The sites of some institutions and organizations of the US government collapsed. The most important servers have suffered data loss. The global network-based instant cyber attack measurement service took offense from NorseCrop[3] and was disabled. Based on the estimates, these attacks costed $ 7 billion to the United States.
How did the cyber attack take place?
On October 21st, the world’s most popular web sites like Twitter, Spotify, Netflix, Reddit, Paypal, Shopify, Box, Etsy, Github, HBONow, AirBnB, Pinterest, Starbucks, Wired, hundreds of thousands of webcams and digital video recorders were exposed the most dangerous attack on computer networks to date. The links to web pages were cut off.
The attack first targeted Twitter, Paypal and Spotify, which used DynDNS’s infrastructure. One of the most dangerous type of cyber attacks, the botnet, was used by the hackers. The “botnets”, which was a type of DDoS (Distributed Denial of Service) attack, sent malicious code from hundreds of thousands of devices internally connected to the platforms. This type of cyber attack was on the agenda of the world at the time.
What is DDoS Attack and Botnet?
DDoS attack is an overloaded request from one or more devices to a server, which results in making the server unreachable. Suppose that you have a web server with a request processing speed of 400 packets. If you send 401 packets to this server at the moment, this server becomes unable to process packets and becomes temporarily out of service.
That’s exactly what hackers do. Then, how do hundreds of thousands of requests be sent simultaneously? BOTNET is the answer to this question. The concept that we call botnet is basically the sum of devices controlled by hackers. If a hacker takes control of 100 security cameras, 100 computers and 200 mobile phones, he can send 400 packets to the server at a time and can easily disable the server. The attack on the United States was very similar one. Of course this time we’re talking about 1 million devices, not 400. In Figure 1[4], the concept of botnet is depicted to be understood more clearly.
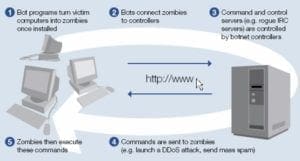
Figure-1[3] Concept of Botnet
The e-mail of Hillary Clinton,
The issue is seven years ago when Hillary Clinton became Foreign Secretary. Clinton sent business and personal electronic mail from hdr22@clintonemail.com instead of opening an official .gov extension email address. The e-mail of Hillary Clinton, the Democratic Party’s presidential candidate in the US, had been debated for months before the Federal Bureau of Investigation (FBI) decided to start a new inquiry expectedly, and the issue was once again the first item in the agenda of the country.
Based on the results of the surveys, Clinton was 12 points ahead before the investigation started.The publications that WikiLeaks sustained throughout her campaign reinforced the perception that Clinton and her team are politically weak.
As the election day approached, it was clear that the information obtained from cyber attacks was used by Trump as propaganda through social media. The Democratic Party and its candidate Clinton had a public reputation problem and could not prevent undecided supporters from voting for Trump. It had an important affect on Trump’s victory.
The effects of these three cyber attacks are demonstrated in the following graphs, which show the results of the surveys made before the attacks and the actual election results The graphics help us to see the effect of the cyber attacks clearly. On Public Research (50 States) 6 September in Figure 2, The Democratic Party is shown in blue and has 228 delegates, while the Republican Party has a red color and 126 delegates, the undecided is gray and 126 delegates, while in the election results on November 8 in Figure 3, the blue colors turn red with blue and It is clear that the undecideds voted the Republican Party. In this case, the voter turns out to be a crucial influence on the decision changes, the result of the cyber attacks, the result of the propaganda material, and the decision changes.
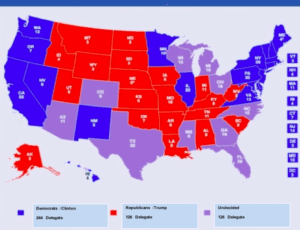
Figure-2 Map: Washington Post Public Research (50 States) 6 September |

Figure-3 Map: Washington Post US Election Results 8 November |
The cyber attacks that Russians made can be liken to a preparation match before the real match, which is elections. The end result of the preparation match streng then their belief that they would achieve the victory they want in the elections.
There is a known fact that Russian intelligence has reached the elements of many state or local election boards. Since early 2014, Russian intelligence has explored US electoral processes and related technology and equipment as well. The recent report[5] by Bitdefender Labs clear that the Russian IRON TWILIGHT (also known as APT28, Pawn Storm, Sofia, Tsar Team, Stronsium and Fancy Bear) in 2016 has carried out “active measures” operations aimed at influencing the US presidential election. I believe without doubt that there were various attacks both in the voting process and in the counting of votes. We might also hear these kind of statements from the authorities in the future.
It is difficult to predict what will happen in the following periods, but investigations conducted on this issue and the data obtained will lead to greater surprises than ,the results of the elections
Consequently; US elections are not the first experience of Russian style cyber attacking. The outcome of the attacks on Ukraine, Estonia, Georgia and Moldova, all of which have long been recognized by United States. The common feature of the victorious candidates in those countries is that they are all in favor of Putin. US elections; The most prominent example of the information obtained from cyber attacks is how politically the propaganda material is made and the results of the election change contrary to expectations.
Some researchers expect similar operations on the elections of some other countries that Russian government is strategically interested in. These elections may include the French presidential and German federal elections.
Jr. T.BAT.
[1] https://www.intelligence.senate.gov/sites/default/files/documents/ICA_2017_01.pdf
[2] www.chicagotribune.com Ellen Nakashima The Washington Post
[3] NorseCorp is a service that show all the world’s cyber attacks on a real-time and interactive map http://map.norsecorp.com
[4] Figure-1: http://www.aic.gov.au/publications/current%20series/tandi/321-340/tandi333.html
[5] https://www.infosecurity-magazine.com/news/russian-election-hackers-target/

