
Terrorist groups always strive to outmaneuver counter-terrorism agencies with different tactics and strategies for making successful attacks. Therefore, understanding unexpected attacks is becoming more and more important. Studying such attacks will help identify the strategies from past events that will be most dangerous when counter-terrorism agencies are not ready for protection interventions. In this paper, we propose a new approach that defines terrorism outliers in the current location by using non-similarities among attacks to identify unexpected interactions.
The approach is used to determine possible outliers in future attacks by analyzing the relationships among past events. In this approach, we calculate the relationship between selected features based on a proposed similarity measure that uses both categorical and numerical features of terrorist activities. Therefore, extracting relations are used to build the terrorist network for finding outliers. Experimental results showed that the comparison of actual events and the detected patterns match with more than 90% accuracy for many future strategies. Based on the properties of the outliers, counter-terrorism agencies can prevent a future bombing attack on strategic locations.
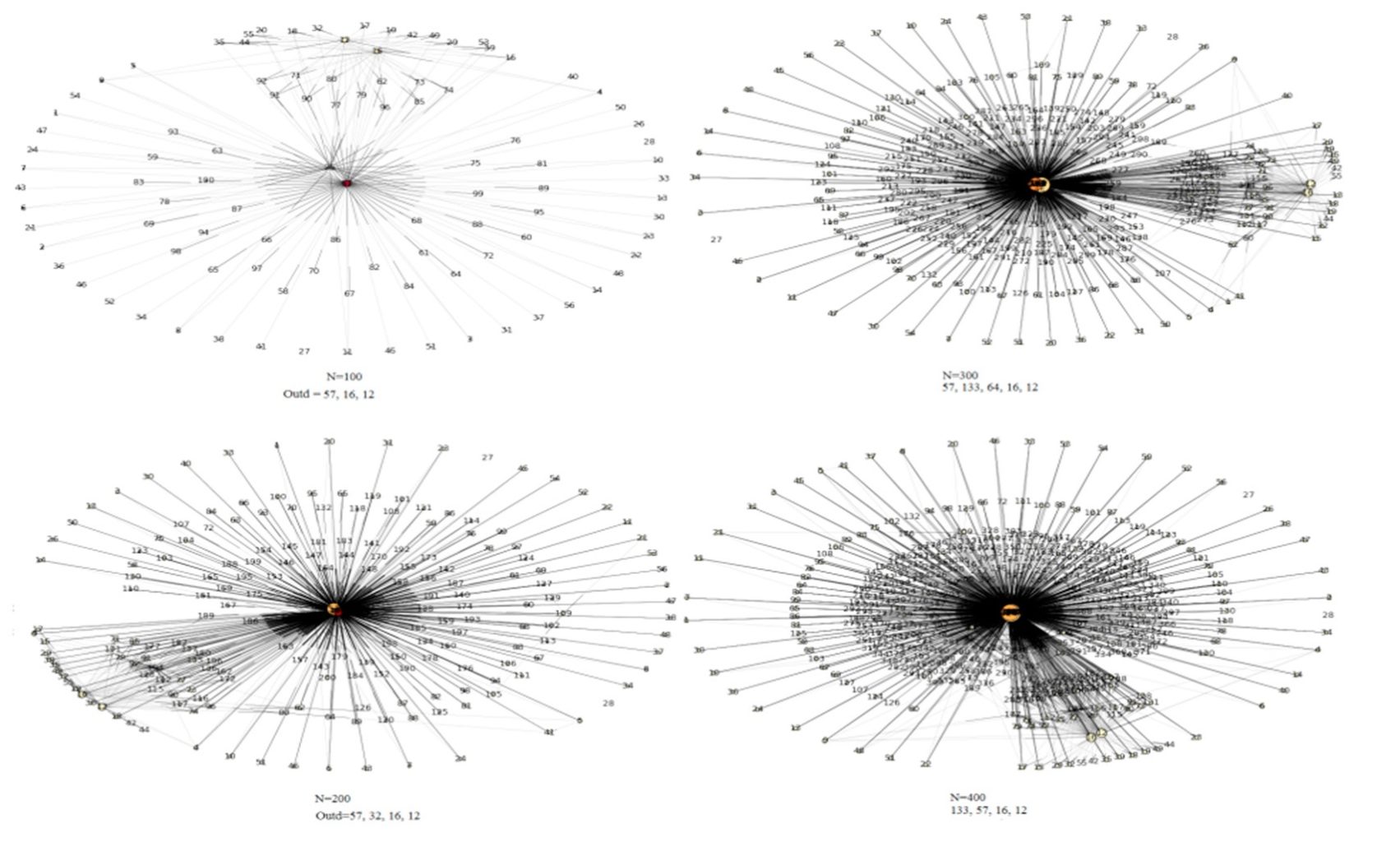
Defining outliers for future attacks.
As seen in the above Figure, we calculated the similarity of outlier attacks for the next 100 attacks with high accuracy. Therefore, we can understand outlier behaviors for future attacks. As a result, based on non-similar relations, we can find outlier behaviors for future attacks. When defenders focus on these actions, they can understand which behaviors are unused and have a high potential for occurrence in the future.
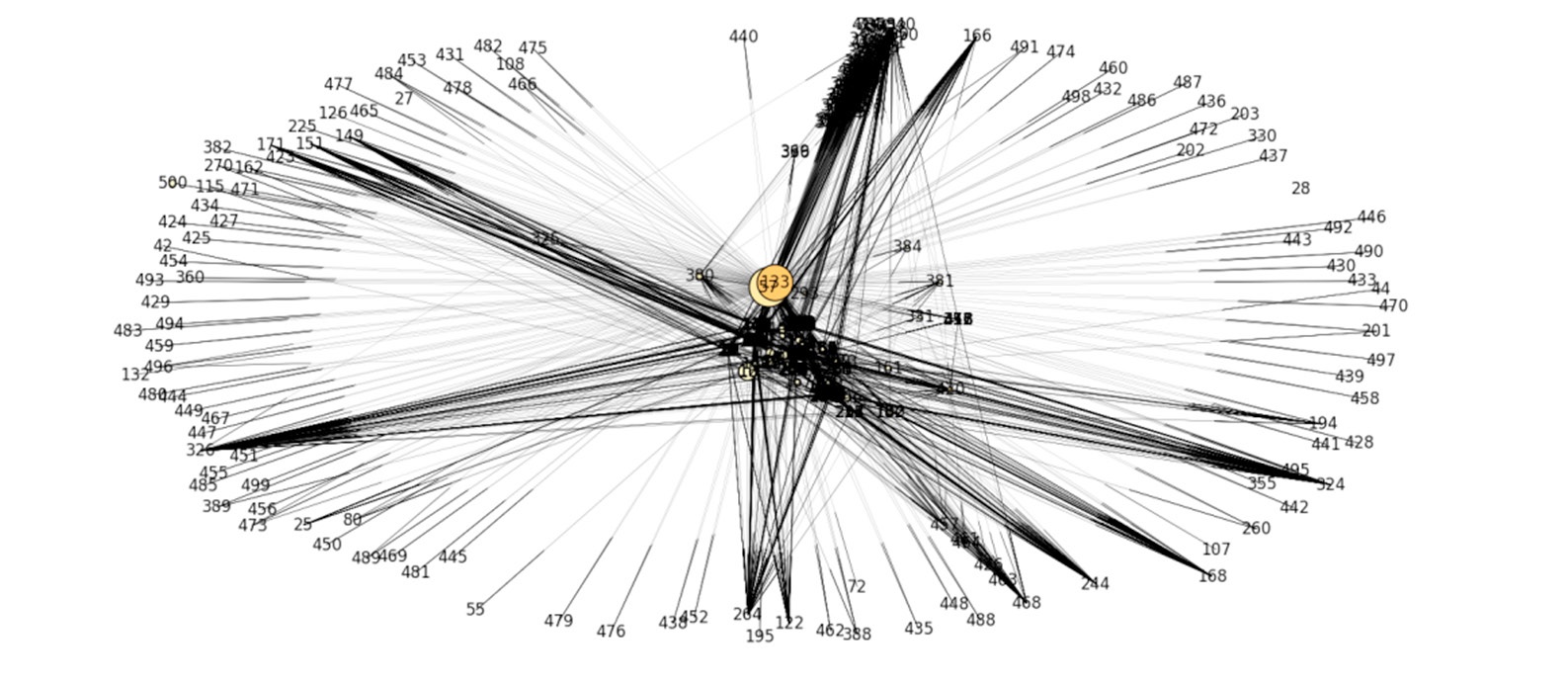
Defining the most important outliers for future attacks.
Furthermore, some events when followed all past attacks, are found as the most non-similar for using future events. As seen in the above Figure, Event 57 and Event 133 have successful strategies in the past attacks. Once attackers used these strategies, they will shock defenders with successful attacks. In order to control attackers, defenders need to analyze these events deeply. They also continue to search other events dynamically. In this way, attackers can be controlled to prevent the most dangerous attacks.
Conclusions
Nowadays, counter-terrorism agencies need to develop better defense strategies to combat the attackers’ tactics. This research proposes a new approach based on a similarity function. More specifically, a heterogeneous similarity function is proposed to analyze relationships between interactive events to understand how attackers seek to surprise defenders. At the same time, the proposed network approach is different because it uses attackers (as events) instead of people.
The proposed approach proves its usefulness due to the use of the proposed similarity function. We show that attacks can be prevented by learning from outlier behavior of attacks. The results prove that we can understand outlier behaviors for bombing attacks by finding patterns. The patterns identified with more than 90% accuracy show that the framework can be used to understand future attacks.
In conclusion, defenders can deter threats by using this approach. They can understand how terrorism will impact future events, and governments can control attackers’ behaviors to reduce the risk of future events. After attacks occur, the defenders can understand differences between attacks. The proposed approach enables policymakers to develop precise global and/or local counter-terrorism strategies. Furthermore, this information can be extremely useful for law enforcement agencies, which allows them to propose timely reactive strategies.
* Assistant Professor at Washington University in St. Louis, Senior ML Engineer at Beyond the Horizon ISSG, and Horizon Global Academy Lecturer
“Originally published at becominghuman.ai on 20 Dec 2018.”
Contact
Phone
Tel: +32 (0) 2 801 13 57-58
Address
Beyond the Horizon ISSG
Davincilaan 1, 1932 Brussels

